 Look how old this is!
Look how old this is! I post at SearchCommander.com now, and this post was published 12 years 10 months 5 days ago. This industry changes FAST, so blindly following the advice here *may not* be a good idea! If you're at all unsure, feel free to hit me up on Twitter and ask.
As pointed out over a month ago by Sucuri, brute force attacks on WordPress are on the rise, and this past week the entire web hosting world was rocked by a coordinated and persistent attack on WordPress that has attempted (and continues to attempt) to gain access to millions of WordPress installations.
The ‘official’ details are here in the US Cert Alert.
Not only were our own servers impacted, but so were those at nearly any host you can find, and everyone from NBC News to Tech Crunch is reporting that thousands of sites and and web-hosting reseller servers are being targeted..
As reported by The Verge –
A huge network of over 90,000 IP addresses has been targeting WordPress blog installations with a brute force attack, attempting to gain access by using the default “admin” username by trying multiple passwords.
In our own case, one shared server actually logged over 12,000 requests for access in a one hour period, which of course paralyzes the server, so on Friday we were forced to take additional measures of protection.
How Are Our Hosting Customers Affected?
To combat this, going forward, all PDXTC web hosting customers will now see this login BEFORE being granted access to their WordPress login page –
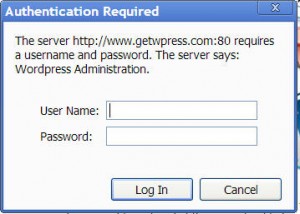
The username and password are *not* your WordPress password, but are one of eight different possibilities, depending upon which server your shared site is located.
What is your access username and password?
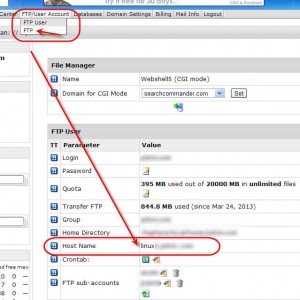
To determine the username and password for your server, log into your web hosting control panel and go to the FTP menu item.
What you see there next to the title “Host Name” will be the name of your server, beginning with the word “linux” and that is the exact username and password for that new login screen.
As soon as you copy & paste that one name into both boxes, you’ll get access to the WP login that you’re looking for. We are very sorry for the inconvenience, but it was a necessary addition.
The Exact Issue:
To be clear, none of our sites were compromised, but the servers were bogged down by attempts.
Automated programs are out roaming the web there looking for every single /wp-admin login page in the world, and then attempting to “guess” the often used ‘admin’ usernames by trying multiple passwords .
Now this is nothing new, and in the past, multiple login attempts from specific IP addresses could be dealt with easily by webhosts or webmasters themselves, by limiting login attempts, or blocking IP addresses entirely, and there are even some plugins that could be used.
With this brute force attack however, the requesting IP address just rotates endlessly through their 90,000 IP address network, so there’s no way to get a handle on who’s trying to get in!
Sadly, it’s an unfortunate byproduct of using the most popular web platform in the world, and we’re sorry for any inconvenience this may cause our hosting clients.
How Else Can You Protect Yourself?
If you’re not a PDXTC hosting customer, there’s no doubt that your own web host has been affected too. If you’ve not heard from them yet, you will soon, trust me. This thing has brought thousands of web servers to their knees in the past 7 days.
Immediately changing your admin passwords is a good start, and this recent Krebs’ post has links to more tools for securing your WP blog. Monitoring your site with something like Sucuri is also a good idea, but ultimately, this might be more of web hosting issue, so contact your provider to see what they recommend…




















Tried this but it’s not working. Has this changed in the last 2 years?
Nope, not at all, but this post was written for our hosting customers, so unless we host your site, it’s not relevant.
Well, recently Brute force Attacks has immensely increased, becoming a dangerous factor for all WordPress users, but it is a thing, which is fight-able, I mean, by using security methods, we can move brute force attacks out of the window. Although, it can be difficult for newbies, who just got started with WordPress, but he/she can learn by reading posts online and then can implement security.
In my view, implementing only three tricks works very well, Changing Login Slug, A content Delivery network (CDN) and a Security Plugin, which bans IP address after a few Login attempts.